Tech
NFC Tag Detected: Complete FAQ In 7 Chapters [Explained]

NFC (Near Field Communication) technology has quietly transformed the way we interact with the world around us. From mobile payments to contactless access control, NFC has seamlessly integrated itself into our daily lives. At the heart of this technology lies the “NFC tag detected” moment, a magical interaction that triggers a plethora of possibilities. In this comprehensive guide, we will delve deep into the world of NFC tag detection, unraveling its intricacies and applications.
Key Takeaways
Before we embark on this journey, let’s highlight some key takeaways that you’ll gain from this guide:
- Understanding NFC Technology: We will explore the fundamentals of NFC technology, explaining how it works and its relevance in modern life.
- Types of NFC Tags: Learn about the different types of NFC tags available and their unique characteristics.
- NFC Tag Detection: Discover the mechanisms behind NFC tag detection and the role of smartphones and other NFC-enabled devices.
- Applications of NFC: Explore a wide range of practical applications, from mobile payments to smart home automation.
- How to Create NFC Tags: Find out how to create and program your own NFC tags for specific purposes.
- Security Considerations: Understand the security implications of NFC technology and how to protect your data.
- Troubleshooting: Learn how to troubleshoot common issues related to NFC tag detection.
Now, let’s delve into the fascinating world of NFC tag detection.

Chapter 1: Understanding NFC Technology
NFC technology is at the heart of the “NFC tag detected” experience. To comprehend this moment fully, it’s essential to understand the fundamentals of NFC technology.
NFC stands for Near Field Communication. It’s a short-range wireless communication technology that allows two devices, typically a smartphone and an NFC tag, to exchange data when they are in close proximity, usually within a few centimeters. This close proximity requirement ensures the security of NFC transactions.
NFC operates on the principles of electromagnetic induction. When an NFC-enabled device, such as a smartphone, comes into close proximity with an NFC tag, it creates a magnetic field that powers the tag. This power enables the tag to transmit data to the device, initiating the “NFC tag detected” event.
NFC supports three communication modes: peer-to-peer, reader/writer, and card emulation. Peer-to-peer mode allows two NFC-enabled devices to exchange data, while reader/writer mode enables a device to read information from an NFC tag. Card emulation mode allows a device to mimic an NFC card, such as a contactless payment card.
Chapter 2: Types of NFC Tags
Not all NFC tags are the same. They come in various forms, each with its own characteristics and use cases.
Passive NFC Tags: Passive tags are the most common type of NFC tag. They don’t have their power source but rely on the electromagnetic field generated by the NFC-enabled device to power up and transmit data. They are widely used in applications like product labeling, marketing materials, and access control.
Active NFC Tags: Active tags, in contrast, have their power source, typically a battery. This allows them to initiate communication without relying on an external power source. Active tags are often used in more complex applications, such as asset tracking and inventory management.
Semi-Passive NFC Tags: These tags have a battery for powering their internal circuitry but rely on the NFC-enabled device’s field to wake up and communicate. They strike a balance between the power efficiency of passive tags and the autonomy of active tags. Applications include temperature sensing and data logging.
Chapter 3: NFC Tag Detection Mechanisms
The “NFC tag detected” event is a result of several intricate mechanisms working together.
Electromagnetic Fields: NFC operates in the radio frequency (RF) range. When an NFC-enabled device and an NFC tag come close, they create an RF electromagnetic field. This field powers up the NFC tag, allowing it to send data back to the device.
Data Transfer Modes: NFC supports various data transfer modes, including NFC-A, NFC-B, and NFC-F. Each mode has its specific frequency and modulation schemes. The NFC-enabled device and the tag must operate on the same mode to communicate effectively.
Data Exchange Protocols: NFC uses standardized protocols like ISO 14443 and ISO 18092 to ensure compatibility between devices and tags. These protocols define how data is formatted and exchanged, ensuring a seamless “NFC tag detected” experience.
Chapter 4: Practical Applications of NFC Technology
The applications of NFC technology are boundless, and the “NFC tag detected” event is the gateway to many of them.
Contactless Payments: NFC technology is the backbone of contactless payment systems like Apple Pay and Google Wallet. When you tap your smartphone or contactless card on a payment terminal, it’s the “NFC tag detected” moment that enables secure transactions.
Transportation: Many public transportation systems worldwide use NFC for ticketing. A simple tap of your NFC-enabled card or smartphone at a turnstile grants you access, thanks to the “NFC tag detected” event.
Healthcare: NFC tags are used in patient identification, medication tracking, and medical equipment management. “NFC tag detected” ensures accurate and secure data exchange in these critical applications.
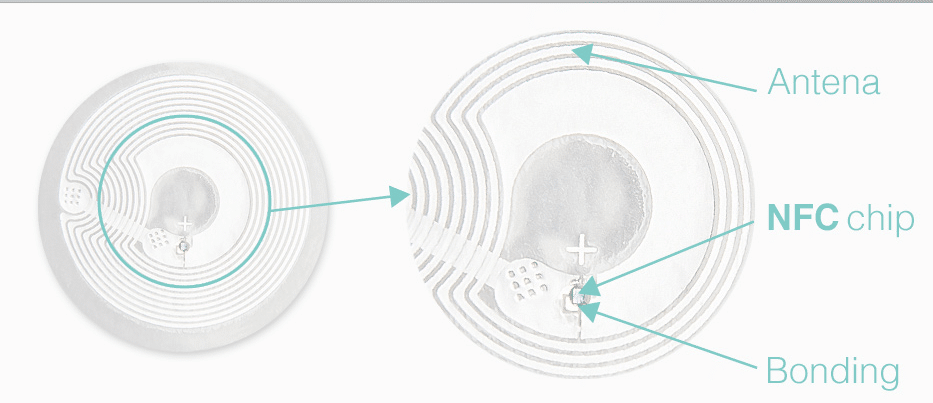
Chapter 5: How to Create and Program NFC Tags
Creating and programming NFC tags empowers you to tailor their functionality to your specific needs and preferences.
The first step in creating your NFC tag is choosing the right type. Consider factors such as your intended use case, required memory capacity, and whether you need a read-only or rewritable tag.
You’ll need an NFC writer/reader, often integrated into smartphones or available as standalone devices, to program your NFC tags. Many NFC writer apps are available for smartphones, simplifying the process.
NFC tags can store various types of data, including URLs, contact information, text messages, and more. Programming involves encoding the desired data onto the tag. For instance, you can program an NFC tag with your business card information so that when someone taps their phone on it, your contact details are instantly added to their contacts.
NFC tags can trigger actions on your smartphone, such as turning on Wi-Fi, enabling Bluetooth, or launching specific apps. This automation can simplify daily tasks and streamline your smartphone experience.
When programming NFC tags, it’s crucial to consider security. For example, you can set a password to restrict access to sensitive data stored on the tag. Understanding these security features is essential to protect your information.
Chapter 6: Security Considerations
Security is paramount when dealing with NFC technology, especially since the “NFC tag detected” moment often involves sensitive data exchange.
To ensure the legitimacy of an NFC transaction, authentication mechanisms can be employed. This may involve cryptographic protocols to verify the identity of the communicating devices and protect against eavesdropping or tampering.
Encrypting the data being transferred during an “NFC tag detected” event adds an additional layer of security. This ensures that even if unauthorized parties intercept the communication, they cannot decipher the information.
NFC technology can inadvertently lead to privacy breaches, such as when malicious actors attempt to read sensitive information from your NFC-enabled devices without your knowledge. Understanding how to protect your devices and data from such threats is vital.
: Some NFC-enabled devices have a secure element, a dedicated hardware component designed to store sensitive information securely. Utilizing the secure element can enhance the security of transactions involving NFC tags.
Chapter 7: Troubleshooting NFC Tag Detection Issues
Occasionally, you might encounter issues with NFC tag detection. Knowing how to troubleshoot these problems can save you time and frustration.
Check NFC Settings: First, ensure that NFC is enabled on your device. It’s a simple step, but it’s often the root cause of detection problems.
Physical Obstacles: NFC relies on close proximity, so ensure that there are no physical barriers between the device and the NFC tag. Cases or covers that block the signal can hinder detection.
Tag Compatibility: Not all NFC tags are compatible with every device. Ensure that the tag you’re trying to read is compatible with your device’s NFC protocol.
Interference: Environmental factors like strong electromagnetic fields or other NFC-enabled devices in the vicinity can interfere with tag detection. Try moving to a different location for better results.
Software Updates: Outdated firmware or software can lead to compatibility issues. Ensure that your device’s firmware and any NFC-related apps are up to date.
Conclusion
In the grand tapestry of modern technology, “NFC tag detected” is a small but significant thread that weaves convenience, efficiency, and innovation into our daily lives. This guide has been your compass, navigating through the intricate world of NFC technology, from its inception to practical implementation.
Armed with knowledge and creativity, you are now poised to unlock the full potential of NFC technology, making your interactions with the digital world seamless and exciting. So, go forth and let “NFC tag detected” be the catalyst for your next technological adventure.
-

 Gadgets6 months ago
Gadgets6 months agoCan Dogs Use VR Headsets?
-

 Tech6 months ago
Tech6 months agoWhat Does “Voicemail Pending” Mean?
-

 Phones5 months ago
Phones5 months agoHow Do I Know if My Phone Supports AR?
-

 Tech5 months ago
Tech5 months agoDoes Astigmatism Affect Your VR Experience?
-

 Business5 months ago
Business5 months agoHow Do You Make an AR Without Coding?
-
 Phones5 months ago
Phones5 months agoWhat To Do About That Weird Notification Sound on Android?
-
 Tech4 months ago
Tech4 months agoHow Can I Get Google Drive 1TB for Free?
-
 Phones4 months ago
Phones4 months agoHow Does SnapDrop Work? – Instant File Sharing Made Easy























